Firewalls are essential for protecting your network, but they can sometimes block legitimate connections, making it difficult to manage IoT devices remotely. This guide will walk you through the process of setting up RemoteIoT on your Mac, even when a firewall is in place. By the end of this article, you'll have a clear understanding of how to configure your system for seamless remote access without compromising security. Whether you're a beginner or an experienced user, this guide is designed to simplify the process and provide actionable steps. RemoteIoT is a powerful platform that allows users to access and manage IoT devices from anywhere in the world. However, when a firewall is involved, the process can become tricky. Firewalls are designed to block unauthorized access, and while this is crucial for security, it can inadvertently block legitimate connections like those required for RemoteIoT. This is particularly true for Mac users, who may face unique challenges due to macOS-specific settings. Understanding how to navigate these challenges is key to ensuring a smooth and secure connection. In this article, we’ll explore the tools, configurations, and best practices you need to overcome firewall restrictions and make the most of RemoteIoT. The importance of securely managing IoT devices cannot be overstated. With the rise of smart homes, industrial automation, and remote work, the ability to access and control IoT devices remotely is more valuable than ever. However, security should never be compromised in the pursuit of convenience. This guide will not only show you how to use RemoteIoT behind a firewall on your Mac but also emphasize the importance of maintaining robust security protocols. By following the steps outlined here, you can ensure that your remote access is both efficient and secure, giving you peace of mind while managing your IoT ecosystem.
Table of Contents
- What is RemoteIoT and Why Use It Behind a Firewall?
- How Does a Firewall Affect RemoteIoT Connections on Mac?
- Step-by-Step Guide to Configuring RemoteIoT Behind a Firewall on Mac
- What Are the Common Challenges When Using RemoteIoT Behind a Firewall?
- How Can You Troubleshoot RemoteIoT Connection Issues on Mac?
- Best Practices for Securing RemoteIoT Connections on Mac
- How to Optimize RemoteIoT Performance Behind a Firewall
- Frequently Asked Questions About Using RemoteIoT Behind a Firewall on Mac
What is RemoteIoT and Why Use It Behind a Firewall?
RemoteIoT is a platform designed to facilitate secure and efficient remote access to IoT devices. Whether you're managing smart home devices, industrial sensors, or remote servers, RemoteIoT provides a reliable way to connect to these devices from anywhere in the world. The platform supports a wide range of devices and operating systems, including macOS, making it a versatile tool for users with diverse needs. By leveraging RemoteIoT, you can monitor, control, and troubleshoot your IoT devices without being physically present, saving time and resources.
Using RemoteIoT behind a firewall is essential for maintaining network security. Firewalls act as a barrier between your internal network and external threats, ensuring that only authorized traffic is allowed through. While this is a critical security measure, it can sometimes block legitimate connections like those required for RemoteIoT. By configuring your firewall to allow RemoteIoT traffic, you can enjoy the benefits of remote access without exposing your network to unnecessary risks. This balance between accessibility and security is what makes RemoteIoT an ideal solution for managing IoT devices in a secure environment.
Read also:Uncut Bold Webseries The Ultimate Guide To Bold Storytelling
Why Choose RemoteIoT Over Other Platforms?
RemoteIoT stands out from other remote access platforms due to its ease of use, compatibility with macOS, and robust security features. Unlike some platforms that require complex configurations, RemoteIoT offers a user-friendly interface that simplifies the setup process. Additionally, its compatibility with macOS ensures that Mac users can take full advantage of its capabilities without worrying about compatibility issues. Security is another key differentiator, as RemoteIoT employs advanced encryption and authentication protocols to protect your data and devices.
How Does a Firewall Affect RemoteIoT Connections on Mac?
Firewalls play a crucial role in network security, but they can also pose challenges when it comes to remote access. On a Mac, firewalls are configured to block incoming and outgoing traffic that doesn't meet specific criteria. This can include traffic from applications like RemoteIoT, which may be flagged as a potential threat if not properly configured. Understanding how firewalls work and their impact on RemoteIoT connections is the first step toward resolving these issues.
What Are the Key Firewall Settings on Mac?
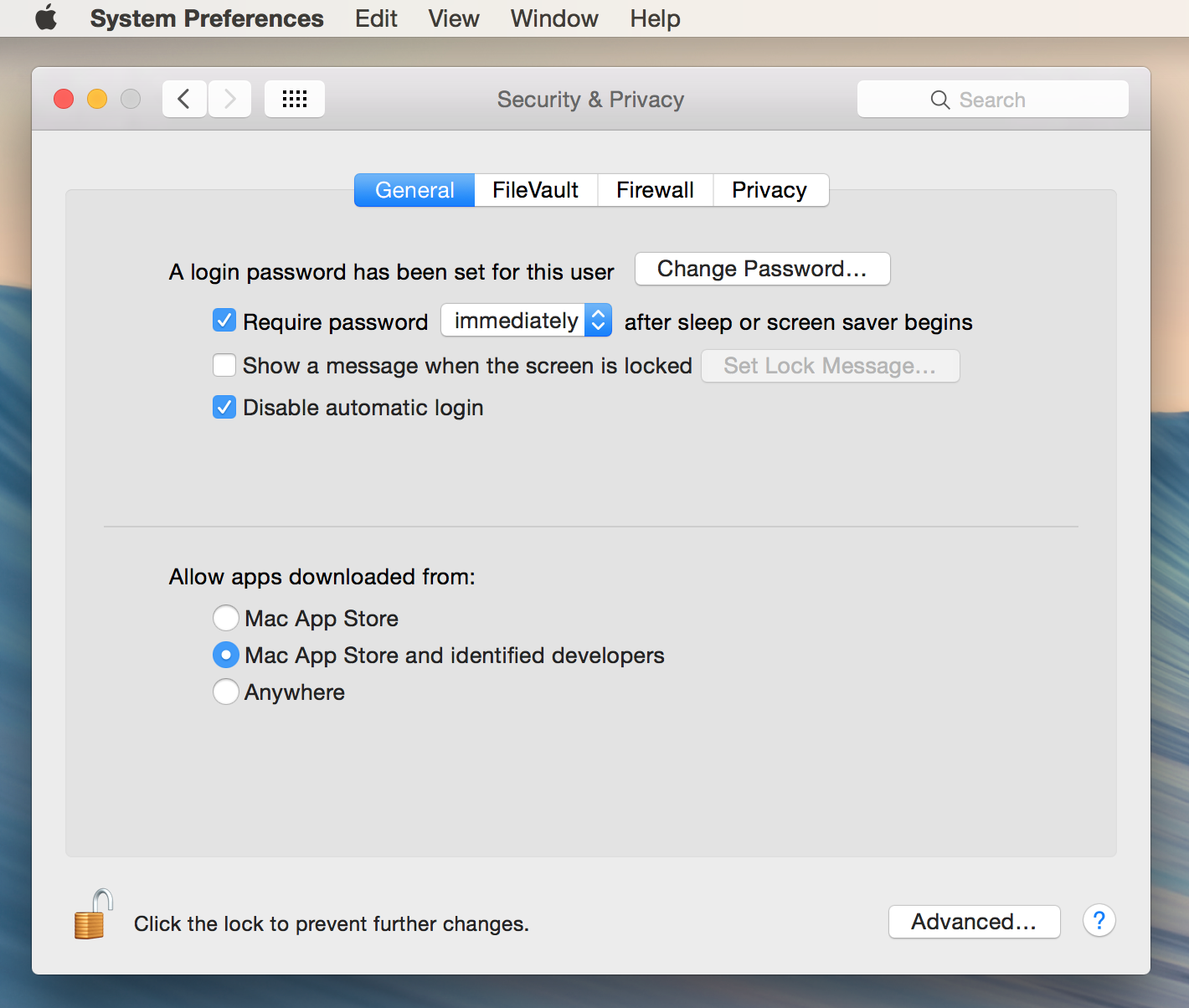
On macOS, the built-in firewall can be accessed through the "Security & Privacy" settings. Here, you can configure which applications are allowed to receive incoming connections. For RemoteIoT to function properly, you'll need to ensure that it is added to the list of allowed applications. Additionally, you may need to adjust advanced settings, such as enabling stealth mode or allowing signed software to communicate. These settings can vary depending on your network environment and security requirements.
How to Add RemoteIoT to Firewall Exceptions
Adding RemoteIoT to your Mac's firewall exceptions is a straightforward process. Begin by opening "System Preferences" and navigating to "Security & Privacy." From there, select the "Firewall" tab and click the lock icon to make changes. Once you've unlocked the settings, click "Firewall Options" and add RemoteIoT to the list of allowed applications. This will ensure that the application can communicate through the firewall without being blocked.
Step-by-Step Guide to Configuring RemoteIoT Behind a Firewall on Mac
Configuring RemoteIoT behind a firewall on your Mac involves several steps, each of which is crucial for ensuring a secure and functional connection. Follow these steps carefully to set up RemoteIoT without compromising your network's security.
- Install RemoteIoT: Begin by downloading and installing the RemoteIoT application on your Mac. Ensure that you're using the latest version to benefit from the most up-to-date features and security patches.
- Configure Firewall Settings: Navigate to your Mac's firewall settings and add RemoteIoT to the list of allowed applications. This will prevent the firewall from blocking the application's traffic.
- Set Up Port Forwarding: If your network uses a router, you may need to configure port forwarding to allow RemoteIoT traffic to pass through. Consult your router's documentation for specific instructions.
- Test the Connection: Once the configuration is complete, test the connection to ensure that RemoteIoT is functioning as expected. If you encounter issues, refer to the troubleshooting section of this guide.
What Are the Common Challenges When Using RemoteIoT Behind a Firewall?
While configuring RemoteIoT behind a firewall on your Mac, you may encounter several challenges. These can range from firewall settings that are too restrictive to issues with port forwarding or network configuration. Understanding these challenges and how to address them is key to a successful setup.
Read also:Discover The Best Of Entertainment With Mixtvnowcom Your Ultimate Streaming Guide
How to Overcome Restrictive Firewall Settings
Restrictive firewall settings can block RemoteIoT traffic, preventing you from accessing your IoT devices. To overcome this, you may need to adjust your firewall's rules to allow specific types of traffic. This can include opening specific ports or allowing traffic from trusted IP addresses. Always ensure that these changes align with your network's security policies to avoid introducing vulnerabilities.
How Can You Troubleshoot RemoteIoT Connection Issues on Mac?
Troubleshooting RemoteIoT connection issues on your Mac involves identifying the root cause of the problem and implementing a solution. Common issues include firewall blocks, incorrect port forwarding settings, and software conflicts. By following a systematic approach, you can quickly resolve these issues and restore your connection.
Steps to Diagnose and Fix Connection Problems
- Check Firewall Settings: Ensure that RemoteIoT is allowed through the firewall.
- Verify Port Forwarding: Confirm that the correct ports are open on your router.
- Restart Devices: Sometimes, simply restarting your Mac and router can resolve connectivity issues.
Best Practices for Securing RemoteIoT Connections on Mac
Securing your RemoteIoT connections is essential for protecting your data and devices. By following best practices, you can minimize the risk of unauthorized access and ensure a safe remote connection.
Use Strong Authentication Methods
Always use strong passwords and enable two-factor authentication (2FA) for an added layer of security. This will help prevent unauthorized users from accessing your RemoteIoT account.
How to Optimize RemoteIoT Performance Behind a Firewall
Optimizing RemoteIoT performance behind a firewall involves fine-tuning your network settings and ensuring that your devices are configured for maximum efficiency. This includes optimizing bandwidth usage, reducing latency, and ensuring that your firewall rules are as permissive as necessary without compromising security.
Frequently Asked Questions About Using RemoteIoT Behind a Firewall on Mac
1. How do I know if my firewall is blocking RemoteIoT?
If you're unable to connect to RemoteIoT, check your firewall settings to ensure that the application is allowed through. You can also consult your network administrator for assistance.
2. Can I use RemoteIoT without modifying my firewall settings?
While it's possible to use RemoteIoT without modifying your firewall settings, doing so may result in connection issues. Adjusting your firewall settings is recommended for a seamless experience.
3. Is RemoteIoT compatible with all versions of macOS?
RemoteIoT is compatible with most modern versions of macOS. However, it's always a good idea to check the platform's system requirements to ensure compatibility.
Conclusion
Using RemoteIoT behind a firewall on your Mac may seem daunting at first, but with the right knowledge and tools, it's entirely achievable. By following the steps outlined in this guide, you can configure your system for secure and efficient remote access. Remember to prioritize security by implementing best practices and troubleshooting any issues that arise. With RemoteIoT, you can manage your IoT devices with confidence, knowing that your network is protected.
For more information on securing your network, you can refer to this external resource.