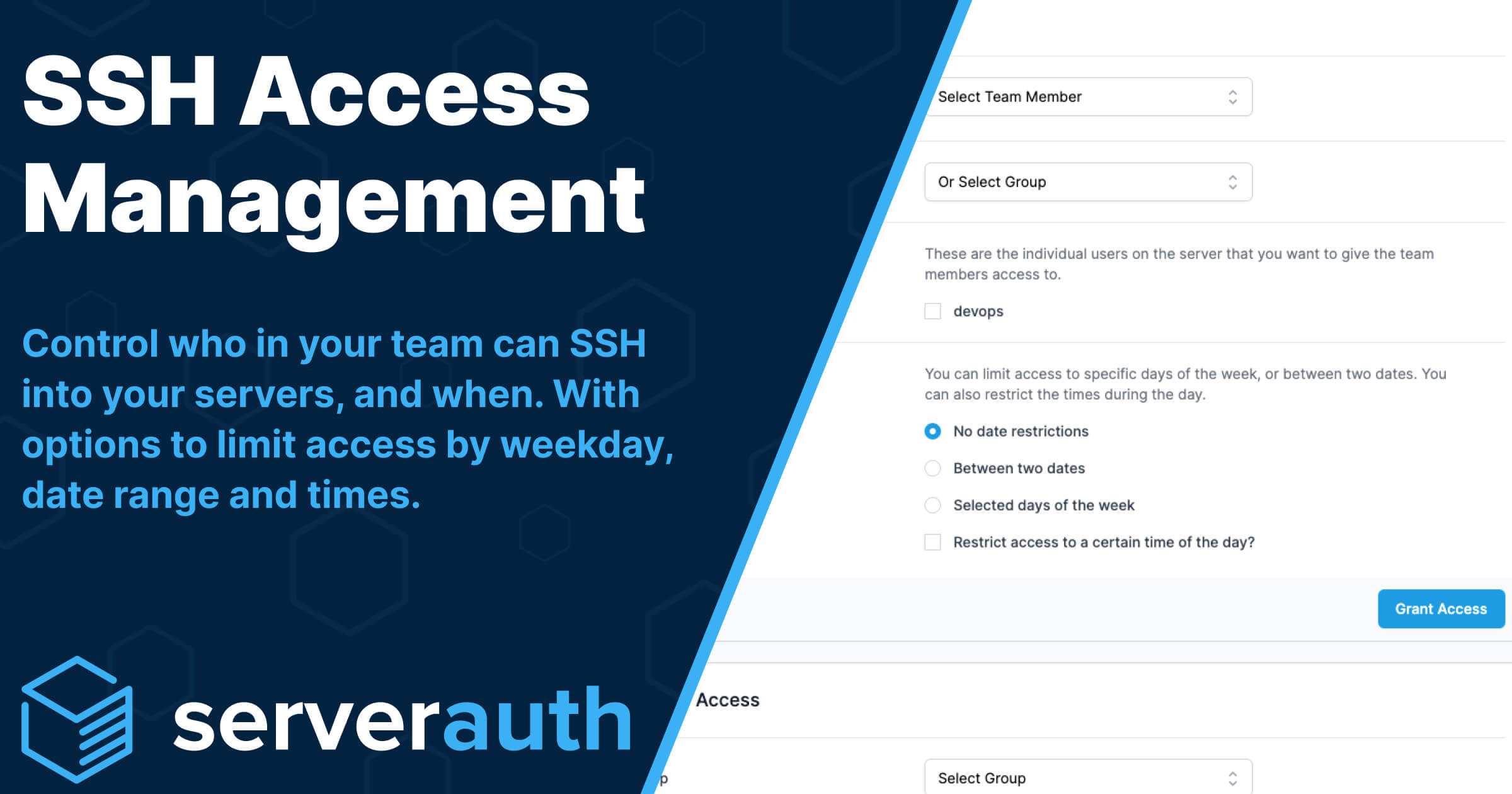
In today’s interconnected digital landscape, monitoring SSH access has become a cornerstone of cybersecurity. Secure Shell (SSH) is widely used for secure remote access to servers, but its misuse can lead to devastating breaches. Organizations must ensure they are vigilant in tracking SSH activity to detect unauthorized access, prevent data breaches, and maintain compliance with security standards. With cyberattacks becoming increasingly sophisticated, understanding how to monitor SSH access is no longer optional—it’s a necessity. This article will delve into the importance of SSH monitoring, tools you can use, and actionable steps to implement robust monitoring practices.
SSH access provides a secure channel over an unsecured network, making it an attractive target for malicious actors. Monitoring SSH access helps you identify suspicious login attempts, track user activity, and ensure only authorized individuals gain entry to your systems. Whether you’re managing a small business server or overseeing enterprise-level infrastructure, implementing SSH monitoring can significantly reduce your risk exposure. Let’s explore the critical aspects of SSH monitoring and how you can fortify your security posture.
From understanding the basics of SSH to deploying advanced monitoring tools, this guide will equip you with the knowledge and tools to protect your systems. By the end of this article, you’ll have a clear roadmap for implementing effective SSH monitoring strategies and ensuring your organization’s digital assets remain secure. Let’s dive into the details and uncover how monitoring SSH access can transform your cybersecurity efforts.
Read also:Who Is Lil Baby Married To Discovering The Life Of A Rising Star
Table of Contents
- Why Is Monitoring SSH Access Critical?
- How Does SSH Work and Why Is It Vulnerable?
- What Are the Best Tools for Monitoring SSH Access?
- Step-by-Step Guide to Implementing SSH Monitoring
- How Can You Analyze SSH Logs Effectively?
- What Are the Common Signs of Unauthorized SSH Access?
- How to Secure SSH Access Beyond Monitoring?
- FAQs About Monitoring SSH Access
Why Is Monitoring SSH Access Critical?
Monitoring SSH access is not just a best practice; it’s a critical component of any cybersecurity strategy. SSH is a protocol that allows secure remote access to servers, but its misuse can lead to unauthorized access, data breaches, and system compromises. Without proper monitoring, organizations risk exposing sensitive data and falling victim to cyberattacks.
One of the primary reasons monitoring SSH access is essential is the rise in brute-force attacks. Hackers often use automated tools to guess SSH credentials, attempting thousands of login combinations until they gain access. By monitoring SSH logs, administrators can detect unusual login attempts and block suspicious IP addresses before they cause harm. This proactive approach not only protects your systems but also helps maintain trust with clients and stakeholders.
Additionally, monitoring SSH access ensures compliance with industry regulations. Many standards, such as GDPR and HIPAA, require organizations to track and audit access to sensitive systems. By implementing SSH monitoring, you can generate detailed reports and demonstrate adherence to these regulations. This not only safeguards your organization from legal repercussions but also enhances your reputation as a security-conscious entity.
How Does SSH Work and Why Is It Vulnerable?
SSH, or Secure Shell, is a cryptographic network protocol designed to provide secure communication over unsecured networks. It encrypts data during transmission, ensuring confidentiality and integrity. However, despite its robust security features, SSH is not immune to vulnerabilities.
SSH works by establishing a secure connection between a client and a server. When a user attempts to log in, the server authenticates the client using credentials such as passwords or SSH keys. While this process is secure, it becomes vulnerable if weak passwords are used or if SSH keys are mishandled. Hackers exploit these weaknesses to gain unauthorized access.
Another vulnerability lies in outdated SSH configurations. Many organizations fail to update their SSH software, leaving them exposed to known exploits. Additionally, default settings like open port 22 can attract attackers. Understanding these vulnerabilities is the first step toward implementing effective monitoring and mitigation strategies.
Read also:What Does Ig Mean In Chat Understanding Its Meaning And Usage
What Are the Best Tools for Monitoring SSH Access?
Choosing the right tools for monitoring SSH access is crucial for maintaining robust security. Several tools on the market offer advanced features to track SSH activity, analyze logs, and generate alerts. Below are some of the best options available:
- Fail2Ban: This open-source tool monitors SSH logs and automatically bans IP addresses that exhibit malicious behavior. It’s highly configurable and integrates seamlessly with firewalls.
- OSSEC: A host-based intrusion detection system (HIDS) that provides real-time log analysis and alerting. OSSEC can detect unauthorized SSH access attempts and notify administrators immediately.
- Splunk: A powerful data analytics platform that can aggregate SSH logs from multiple sources and provide detailed insights. Splunk’s dashboards make it easy to visualize SSH activity and identify anomalies.
- Graylog: An open-source log management tool that centralizes SSH logs and offers advanced search capabilities. Graylog is ideal for organizations that need scalable solutions for monitoring SSH access.
Each of these tools has its strengths, so the choice depends on your organization’s specific needs and budget. Regardless of the tool you select, implementing it correctly is key to ensuring effective SSH monitoring.
Step-by-Step Guide to Implementing SSH Monitoring
Step 1: Enable Logging for SSH Activity
Before you can monitor SSH access, you need to ensure that logging is enabled on your servers. Most Linux distributions come with SSH logging pre-configured, but it’s important to verify and customize the settings to suit your needs.
To enable SSH logging, open the SSH configuration file (usually located at /etc/ssh/sshd_config) and ensure the following lines are present:
LogLevel INFO SyslogFacility AUTH
These settings ensure that all SSH activity is logged and categorized under the authentication facility. After making changes, restart the SSH service to apply the configuration:
sudo systemctl restart ssh
Step 2: Configure Alerts for Suspicious Activity
Once logging is enabled, the next step is to set up alerts for suspicious SSH activity. Tools like Fail2Ban and OSSEC can automatically detect and respond to anomalies, but you can also configure custom alerts using scripts or monitoring platforms.
For example, you can create a script that scans SSH logs for failed login attempts and sends an email notification if a threshold is exceeded. Here’s a simple Bash script to get you started:
#!/bin/bash THRESHOLD=5 FAILED_ATTEMPTS=$(grep "Failed password" /var/log/auth.log | wc -l) if [ $FAILED_ATTEMPTS -gt $THRESHOLD ]; then echo "High number of failed SSH login attempts detected!" | mail -s "SSH Alert" admin@example.com fi
Schedule this script to run periodically using cron to ensure continuous monitoring.
How Can You Analyze SSH Logs Effectively?
Analyzing SSH logs is a critical step in monitoring SSH access. Logs contain valuable information about login attempts, user activity, and potential security threats. However, manually reviewing logs can be time-consuming and error-prone. To analyze SSH logs effectively, consider the following strategies:
First, use log management tools like Splunk or Graylog to centralize and organize your logs. These platforms allow you to search, filter, and visualize data, making it easier to identify patterns and anomalies. For example, you can create dashboards that display failed login attempts, successful logins, and geographic locations of users.
Second, leverage automation to streamline the analysis process. Scripts and tools like Fail2Ban can automatically detect suspicious activity and take action, such as blocking IP addresses or sending alerts. By automating routine tasks, you can focus on more complex security challenges and ensure consistent monitoring.
What Are the Common Signs of Unauthorized SSH Access?
Detecting unauthorized SSH access requires vigilance and an understanding of the warning signs. Below are some common indicators that your systems may be compromised:
- Unusual Login Times: If you notice login attempts occurring at odd hours, it could indicate unauthorized access.
- Repeated Failed Login Attempts: A high number of failed login attempts from the same IP address is a red flag.
- Unknown User Accounts: Check for accounts that you don’t recognize or haven’t created.
- Unexpected File Changes: Unauthorized access often involves modifying or deleting files.
By staying alert to these signs, you can take swift action to mitigate potential threats and protect your systems.
How to Secure SSH Access Beyond Monitoring?
While monitoring SSH access is essential, it’s only one piece of the puzzle. To truly secure your systems, you need to implement additional measures that complement monitoring efforts. Below are some strategies to enhance SSH security:
- Use SSH Keys Instead of Passwords: SSH keys are more secure than passwords and reduce the risk of brute-force attacks.
- Change the Default SSH Port: Moving SSH to a non-standard port can deter casual attackers.
- Implement Two-Factor Authentication (2FA): Adding an extra layer of security ensures that even if credentials are compromised, attackers cannot gain access.
- Limit User Access: Restrict SSH access to only those who need it and use role-based access controls to enforce permissions.
By combining these strategies with robust monitoring, you can create a comprehensive security framework that protects your systems from unauthorized SSH access.
FAQs About Monitoring SSH Access
What Should I Do If I Detect Unauthorized SSH Access?
If you detect unauthorized SSH access, act immediately to mitigate the threat. First, isolate the affected system to prevent further damage. Next, review logs to identify the source of the breach and take steps to block the attacker’s IP address. Finally, update your security protocols and notify relevant stakeholders.
Can Monitoring SSH Access Prevent All Cyberattacks?
While monitoring SSH access is a powerful tool, it cannot prevent all cyberattacks. It’s essential to adopt a layered security approach that includes firewalls, intrusion detection systems, and regular audits to address vulnerabilities comprehensively.
Is It Necessary to Use Third-Party Tools for SSH Monitoring?
While it’s possible to monitor SSH access manually, third-party tools offer advanced features and automation that make the process more efficient. Tools like Fail2Ban and Splunk can save time and improve accuracy, making them valuable additions to your security toolkit.
Conclusion
Monitoring SSH access is a vital practice for safeguarding your systems and ensuring compliance with security standards. By understanding the importance of SSH monitoring, leveraging the right tools, and implementing best practices, you can significantly reduce your risk exposure. Remember, cybersecurity is an ongoing process, and staying vigilant is key to protecting your digital assets.
For further reading on SSH security, check out this comprehensive guide on SSH.