In today’s digital-first world, secure and reliable access to cloud resources is more important than ever. RemoteIoT VPC SSH is a game-changing solution designed to help businesses manage their cloud environments with ease and security. This innovative tool allows users to establish secure shell (SSH) connections within a Virtual Private Cloud (VPC), ensuring that sensitive data remains protected while enabling seamless remote operations. By leveraging RemoteIoT VPC SSH, organizations can streamline workflows, enhance collaboration, and maintain compliance with industry standards. Whether you're managing a small startup or a large enterprise, this technology offers the flexibility and control needed to thrive in the modern business landscape.
With the rise of remote work and cloud-based operations, the demand for secure access solutions has skyrocketed. RemoteIoT VPC SSH addresses this need by providing a robust framework for managing SSH connections in a private, isolated network. This ensures that only authorized users can access critical systems, reducing the risk of unauthorized access and data breaches. Moreover, the platform's intuitive interface and advanced features make it accessible even to those without extensive technical expertise.
Businesses across industries are adopting RemoteIoT VPC SSH to optimize their infrastructure and improve operational efficiency. From healthcare to finance, organizations are discovering the benefits of secure, remote access to cloud resources. This article will explore the ins and outs of RemoteIoT VPC SSH, offering practical insights and actionable advice to help you make the most of this powerful tool. Whether you're new to the concept or looking to deepen your understanding, this guide has something for everyone.
Read also:Priscilla Chan Zuckerberg Inspiring Change Through Vision And Action
Table of Contents
- What is RemoteIoT VPC SSH and Why Does It Matter?
- How Does RemoteIoT VPC SSH Work?
- What Are the Key Benefits of Using RemoteIoT VPC SSH?
- How to Set Up RemoteIoT VPC SSH for Your Business?
- Best Practices for Secure SSH Access in RemoteIoT VPC
- What Are the Common Challenges with RemoteIoT VPC SSH and How to Overcome Them?
- Are There Advanced Features in RemoteIoT VPC SSH You Should Know About?
- What Does the Future Hold for RemoteIoT VPC SSH?
What is RemoteIoT VPC SSH and Why Does It Matter?
RemoteIoT VPC SSH is a cutting-edge solution that enables secure shell (SSH) access within a Virtual Private Cloud (VPC). This technology is particularly valuable for businesses that rely on cloud infrastructure to store and manage sensitive data. By creating a private, isolated network within the cloud, RemoteIoT VPC SSH ensures that only authorized users can access critical systems, reducing the risk of data breaches and unauthorized access.
So, why does RemoteIoT VPC SSH matter? In an era where cybersecurity threats are on the rise, businesses need robust tools to protect their digital assets. RemoteIoT VPC SSH offers a secure and efficient way to manage SSH connections, making it an indispensable tool for IT professionals. Whether you're managing a small team or a large enterprise, this solution provides the flexibility and control needed to maintain a secure and productive work environment.
Key Features of RemoteIoT VPC SSH
RemoteIoT VPC SSH comes with a range of features designed to enhance security and usability. Here are some of the most notable ones:
- Private Network Isolation: Ensures that your SSH connections remain within a secure, isolated network.
- Role-Based Access Control: Allows you to define user roles and permissions, ensuring that only authorized personnel can access sensitive systems.
- Automated Key Management: Simplifies the process of managing SSH keys, reducing the risk of human error.
- Real-Time Monitoring: Provides insights into SSH activity, helping you detect and respond to potential threats.
Why Businesses Are Adopting RemoteIoT VPC SSH
Businesses across industries are adopting RemoteIoT VPC SSH for several reasons:
- Enhanced Security: Protects sensitive data from unauthorized access and cyber threats.
- Improved Efficiency: Streamlines workflows by enabling seamless remote access to cloud resources.
- Compliance: Helps organizations meet regulatory requirements by ensuring secure access to systems.
How Does RemoteIoT VPC SSH Work?
Understanding how RemoteIoT VPC SSH works is essential for leveraging its full potential. At its core, this technology operates by creating a secure tunnel within a Virtual Private Cloud (VPC). This tunnel allows users to establish SSH connections to cloud resources without exposing them to the public internet. By isolating these connections within a private network, RemoteIoT VPC SSH minimizes the risk of unauthorized access and data breaches.
The Role of VPC in RemoteIoT SSH
A Virtual Private Cloud (VPC) is a logically isolated section of a public cloud environment. It allows businesses to run their applications and store data in a secure, private network. RemoteIoT VPC SSH leverages this isolation to ensure that SSH connections remain secure and private. Here's how it works:
Read also:Unpacking The Details Of Dan Orlovsky Contract A Comprehensive Guide
- Network Configuration: The VPC is configured with private subnets, routing tables, and security groups to control traffic flow.
- SSH Tunnel Creation: A secure SSH tunnel is established between the user's device and the VPC, ensuring encrypted communication.
- Access Control: Role-based access control (RBAC) is implemented to restrict access to authorized users only.
Why VPC Integration is Crucial for SSH Security
Integrating SSH with a VPC offers several security benefits:
- Reduced Attack Surface: By isolating SSH connections within a private network, the attack surface is significantly reduced.
- Enhanced Encryption: SSH connections are encrypted end-to-end, ensuring that data remains secure during transmission.
- Centralized Management: All SSH activity is logged and monitored within the VPC, providing greater visibility and control.
What Are the Key Benefits of Using RemoteIoT VPC SSH?
RemoteIoT VPC SSH offers a wide range of benefits that make it an essential tool for businesses of all sizes. From enhanced security to improved efficiency, this solution provides everything you need to manage your cloud infrastructure effectively. Let's explore some of the key advantages in detail.
Enhanced Security and Data Protection
One of the primary benefits of RemoteIoT VPC SSH is its ability to provide robust security for your cloud resources. By isolating SSH connections within a private network, this solution minimizes the risk of unauthorized access and data breaches. Additionally, features like role-based access control and automated key management ensure that only authorized users can access sensitive systems.
Streamlined Remote Access
With RemoteIoT VPC SSH, businesses can streamline remote access to cloud resources. This is particularly valuable in today's remote work environment, where employees need secure and reliable access to critical systems from anywhere in the world. By simplifying the process of establishing SSH connections, this solution enhances productivity and collaboration.
Improved Compliance and Regulatory Adherence
Many industries are subject to strict regulatory requirements regarding data security and access control. RemoteIoT VPC SSH helps businesses meet these requirements by providing a secure and auditable framework for managing SSH connections. This ensures that organizations can maintain compliance while protecting sensitive data.
How to Set Up RemoteIoT VPC SSH for Your Business?
Setting up RemoteIoT VPC SSH is a straightforward process that can be completed in a few simple steps. Whether you're a seasoned IT professional or a newcomer to cloud infrastructure, this guide will walk you through the process of configuring your VPC and establishing secure SSH connections.
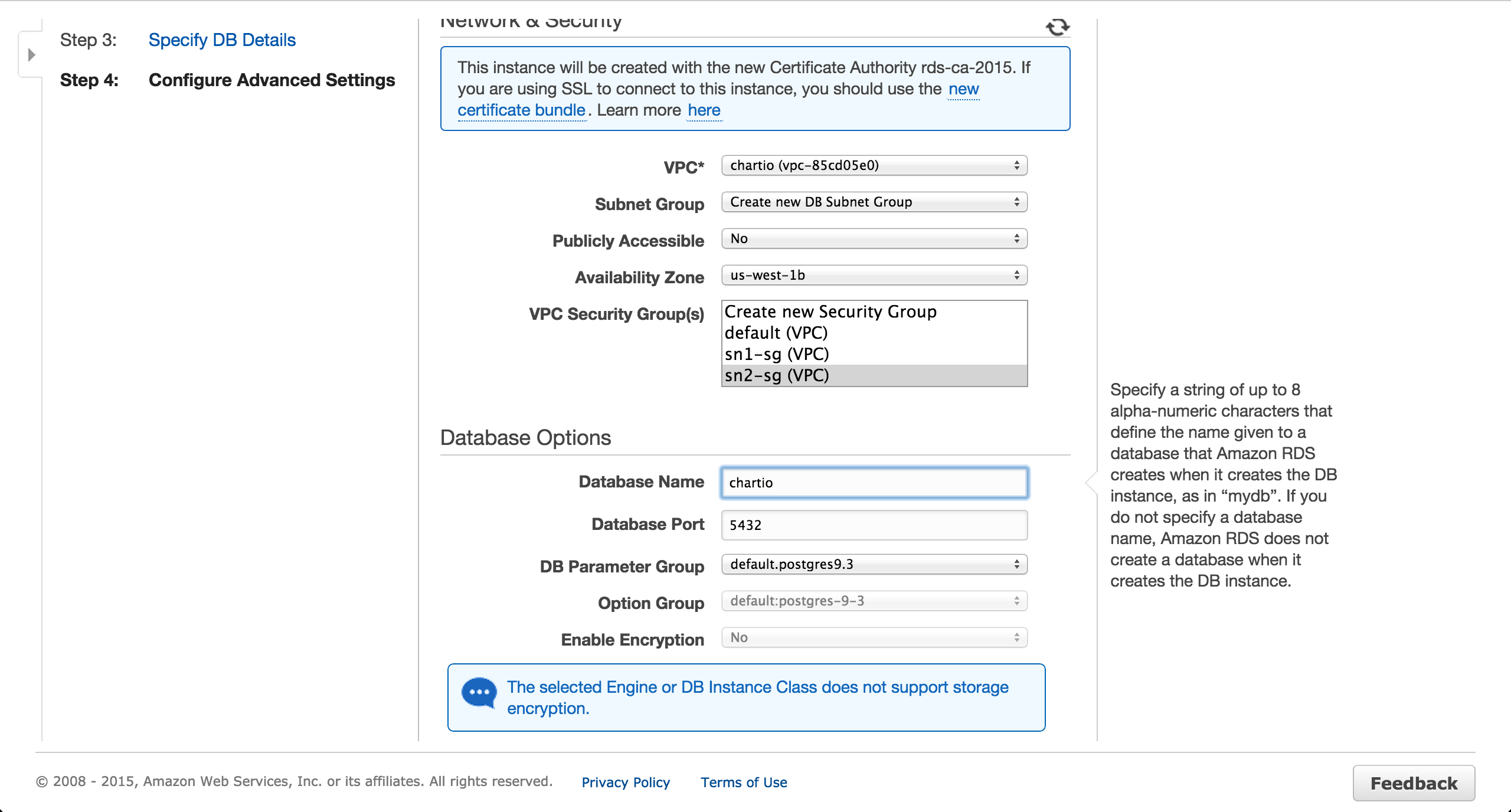
Step 1: Configure Your Virtual Private Cloud (VPC)
The first step in setting up RemoteIoT VPC SSH is configuring your Virtual Private Cloud (VPC). This involves creating private subnets, setting up routing tables, and defining security groups to control traffic flow. Here's how to get started:
- Create a VPC: Use your cloud provider's dashboard to create a new VPC and define its IP address range.
- Set Up Subnets: Divide the VPC into private subnets to isolate different types of traffic.
- Configure Security Groups: Define security rules to control inbound and outbound traffic.
Step 2: Establish SSH Connections Within the VPC
Once your VPC is configured, the next step is to establish SSH connections within the private network. This involves creating SSH keys, configuring access control, and setting up monitoring tools. Here's how to proceed:
- Generate SSH Keys: Use a key generation tool to create public and private SSH keys for each user.
- Define Access Control: Implement role-based access control (RBAC) to restrict access to authorized users only.
- Set Up Monitoring: Use monitoring tools to track SSH activity and detect potential threats.
Step 3: Test and Optimize Your Configuration
After setting up your VPC and SSH connections, it's important to test and optimize your configuration to ensure everything is working as expected. This involves running diagnostic tests, reviewing logs, and making adjustments as needed. Here are some tips to help you get started:
- Run Diagnostic Tests: Use tools like ping and traceroute to verify connectivity and performance.
- Review Logs: Check SSH logs for any errors or unusual activity.
- Make Adjustments: Fine-tune your configuration based on test results and user feedback.
Best Practices for Secure SSH Access in RemoteIoT VPC
Ensuring secure SSH access in RemoteIoT VPC requires a combination of best practices and proactive measures. By following these guidelines, businesses can minimize the risk of unauthorized access and data breaches while maintaining a productive and efficient work environment.
Implement Strong Authentication Protocols
One of the most effective ways to enhance SSH security is by implementing strong authentication protocols. This includes using multi-factor authentication (MFA) and enforcing password complexity requirements. Here are some tips to help you get started:
- Enable Multi-Factor Authentication (MFA): Require users to provide additional verification, such as a one-time code, to access SSH connections.
- Enforce Password Complexity: Require users to create strong passwords that include a mix of letters, numbers, and special characters.
- Regularly Rotate SSH Keys: Periodically update SSH keys to reduce the risk of key compromise.
Monitor and Audit SSH Activity
Monitoring and auditing SSH activity is essential for detecting and responding to potential threats. By keeping a close eye on SSH logs and implementing real-time monitoring tools, businesses can quickly identify suspicious activity and take corrective action. Here are some best practices to consider:
- Enable Real-Time Monitoring: Use tools like intrusion detection systems (IDS) to monitor SSH activity in real-time.
- Review Logs Regularly: Conduct regular audits of SSH logs to identify any unusual patterns or anomalies.
- Set Up Alerts: Configure alerts to notify administrators of potential security incidents.
Limit Access to Authorized Users Only
Restricting SSH access to authorized users only is a critical step in securing your VPC. This can be achieved through role-based access control (RBAC) and network segmentation. Here are some strategies to consider:
- Implement Role-Based Access Control (RBAC